Something I've always struggled with is finding a topic and sticking with it. Becoming an expert in one area. After doing some refresher exercises on x86, I decided to move onto studying the whole Android stack from the moment an Android device powers on and the init file is loaded, kernel archetiture and differences in running Linux on Android, Android IPC using Binder and how Binder serielizes data into messages, Dalvik Runtime and the transition from JIT (Just in Time) to ART (Android Runtime) compilation to the applications themselves.
I was able to get my hands on a few books:
This post is a collection of notes I have gathered from my readings through these books.
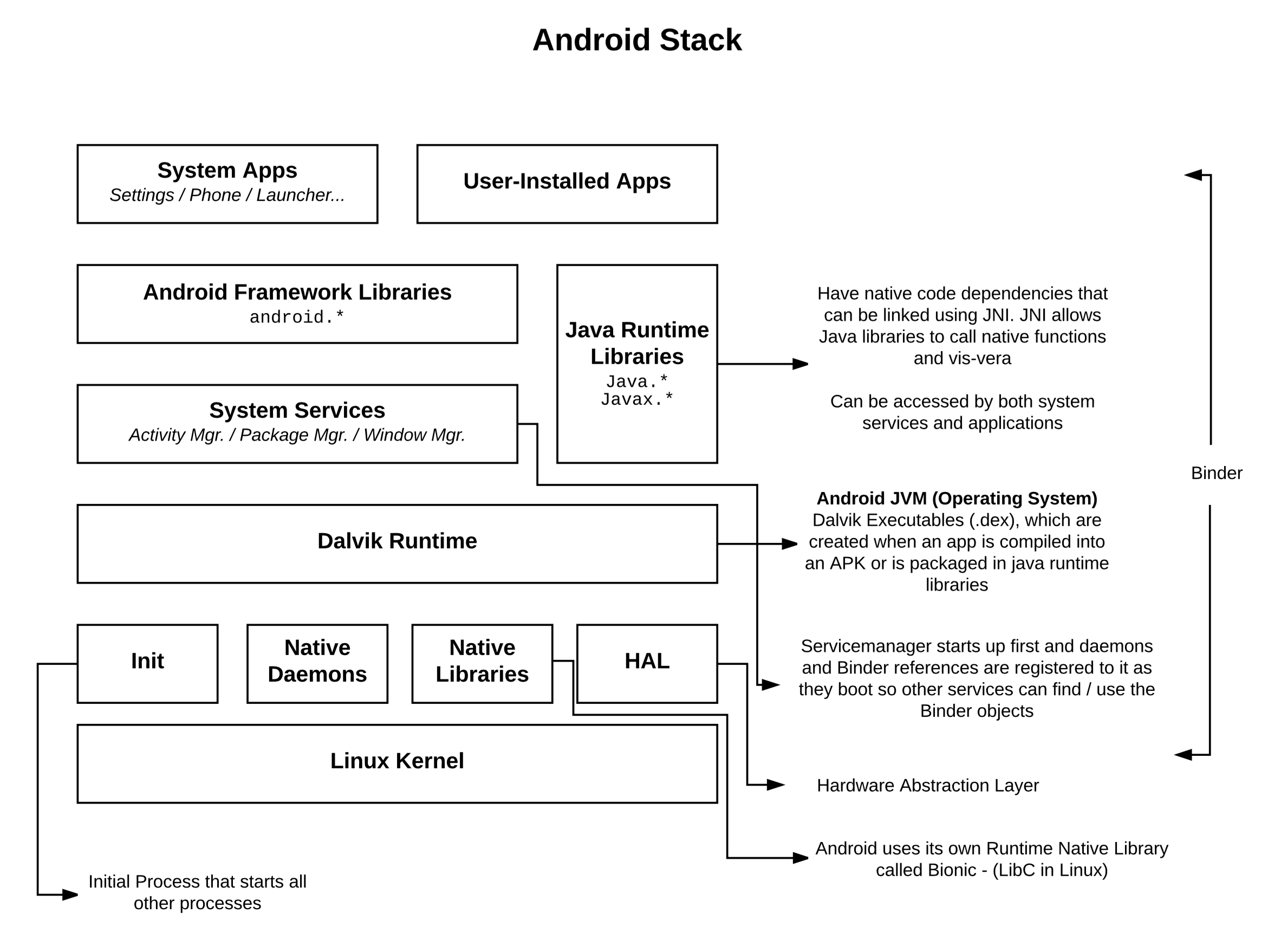
Binder
Binder is the service that handles Interprocess Communication on Android. It works with client / server style of communication and ill try and explain how it works in the simpliest way using this illustration:
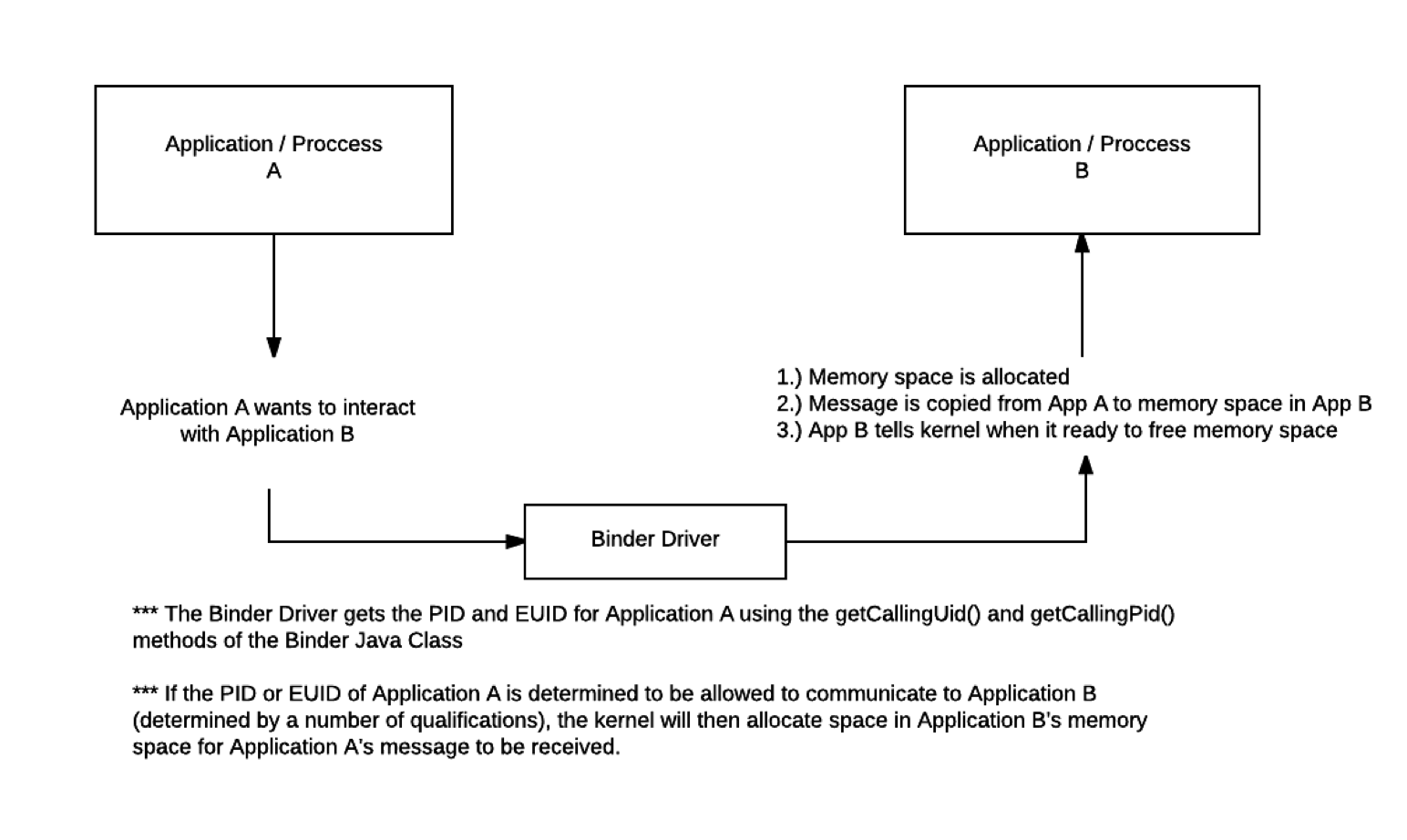
Something to take note here is the getCallingUid() and getCallingPid() methods. Something I did not explain yet is the use of Android Interface Definition Language (AIDL). Everything mentioned above with Binder is used passively without really any user interaction with background processes and etc... However, a developer has the ability to directly call Binder in their application using the Java Class (android.os.Binder) and using AIDL, which is a dirivative of Java designed specifically for Android that will serialize Binder message calls.
Have not really dug into this yet, but the idea of one of the security mechanisms for preventing applications from calling features in other apps is the UID, where mismatched UIDs shouldn't be able to talk to each other. However, it would be interesting to try using Frida to intercept those method calls and change the UID to match the targeted application's with an attacking application.
Dalvik Runtime / JIT / ART
The Android Operating System is a Java Virtual Machine called the 'Dalvik VM' and sits on top of a custom Linux kernel. Skipping the high-level use of the Dalvik VM compiling Java apps into Dalvik Executables, its important to explain Just In Time compilation and Android Runtime.
At the time Android was conceived, JIT was created to be the process for compiling applications, and as you can guess by the name, does this by compiling pieces of the application into Dalvik Bytecode just as that part of that piece of code is going to be used. This was ideal for a 32bit architechture when device requirements were much lower. As the 64bit architechture takes over the mobile industry, the compacity to do so and the need to keep up with iOS, ART was created.
ART allows for the application to be pre-compiled when installed, which allows for a significant increase in performance for the application, but also mainly for the Dalvik VM, as it is no longer dealing with compiling Dalvik Bytecode continuously.
Android Kernel
The Android Kernel only has a few subtle changes compared to a typical Linux Distro. The main one being the config files that the init process loads on boot comprise of specific Android services and hardware, also called Androidisms.
I suggest picking up some reading material if you want to dive into the inner workings of the kernel. The books mentioned will get into Fastboot, Custom Images and the Boot Process/Sequence in great detail and I wouldn't do it any justice laying it out here.
