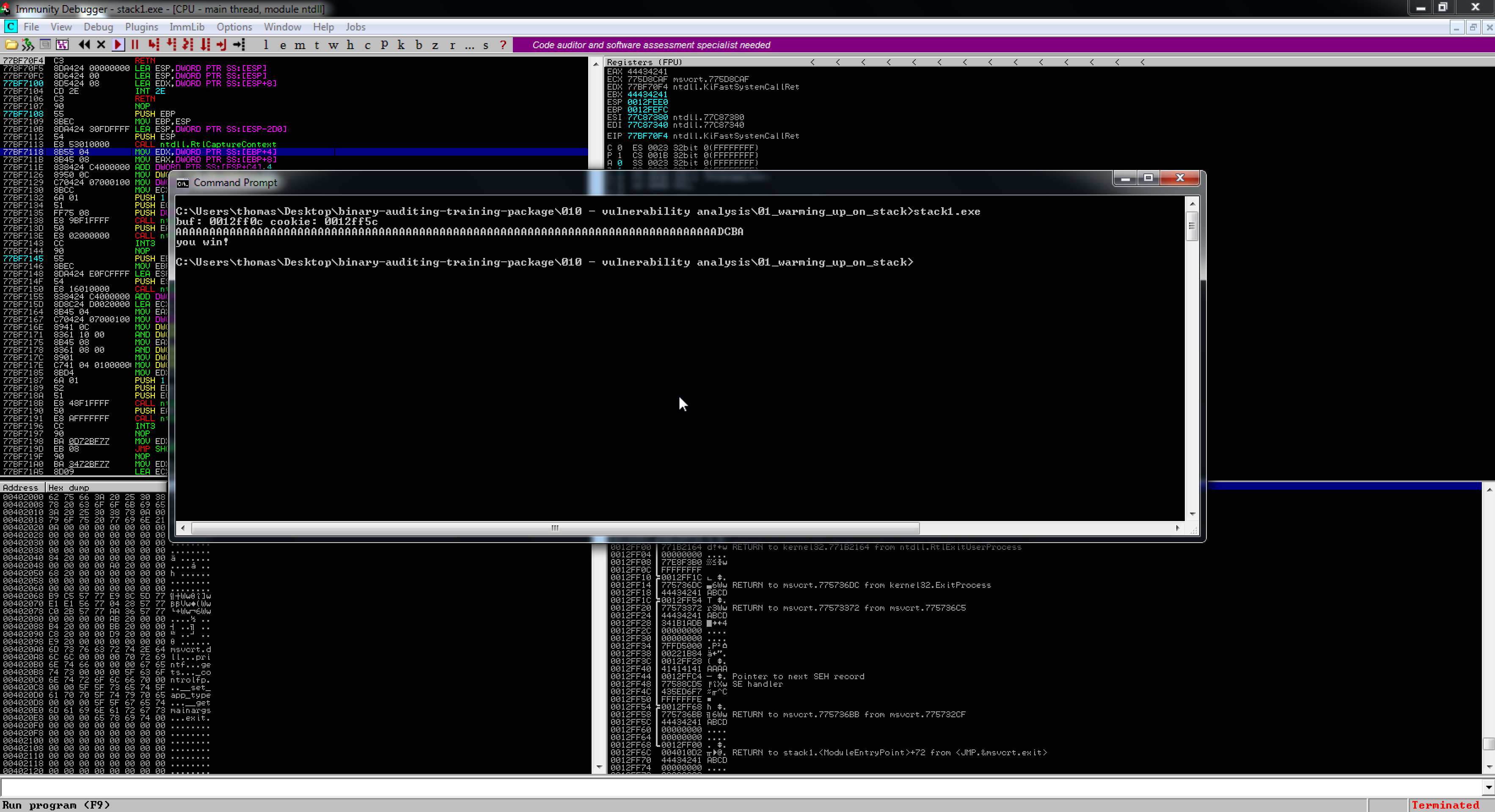
So here we have an executable (stack1.exe) that takes some input and then closes after entering some data. Lets take a closer look in our disassembler to see if we can identify anything else.

sub esp, 0x54 ; creating space for a buffer
lea eax, dword [ebp,+var_4] ; moving the least effective address to eax
push eax ; push eax to stack
lea eax, dword [ebp,+var_54] ; moving the least effective address to eax
push eax ; push eax to stack
; does some printing to the console and takes an argument blah blah
cmp eax, 0x41424344 ; compares string (converted to little endian) of 'ABCD' to eax
jne loc_401049 ; jumps to leave function if eax does not equal 0x41424344
; else, jumps to print 'you win!'
After walking through the program a little bit, we can see that we want to try and get the eax register to equal 0x41424344 in order to make the jump to 'you win!'
I attach the Immunity Debugger to see the memory flow when entering data in the console and find that I can overwrite eax with 84 chars. The last 4 chars being the overwrite.
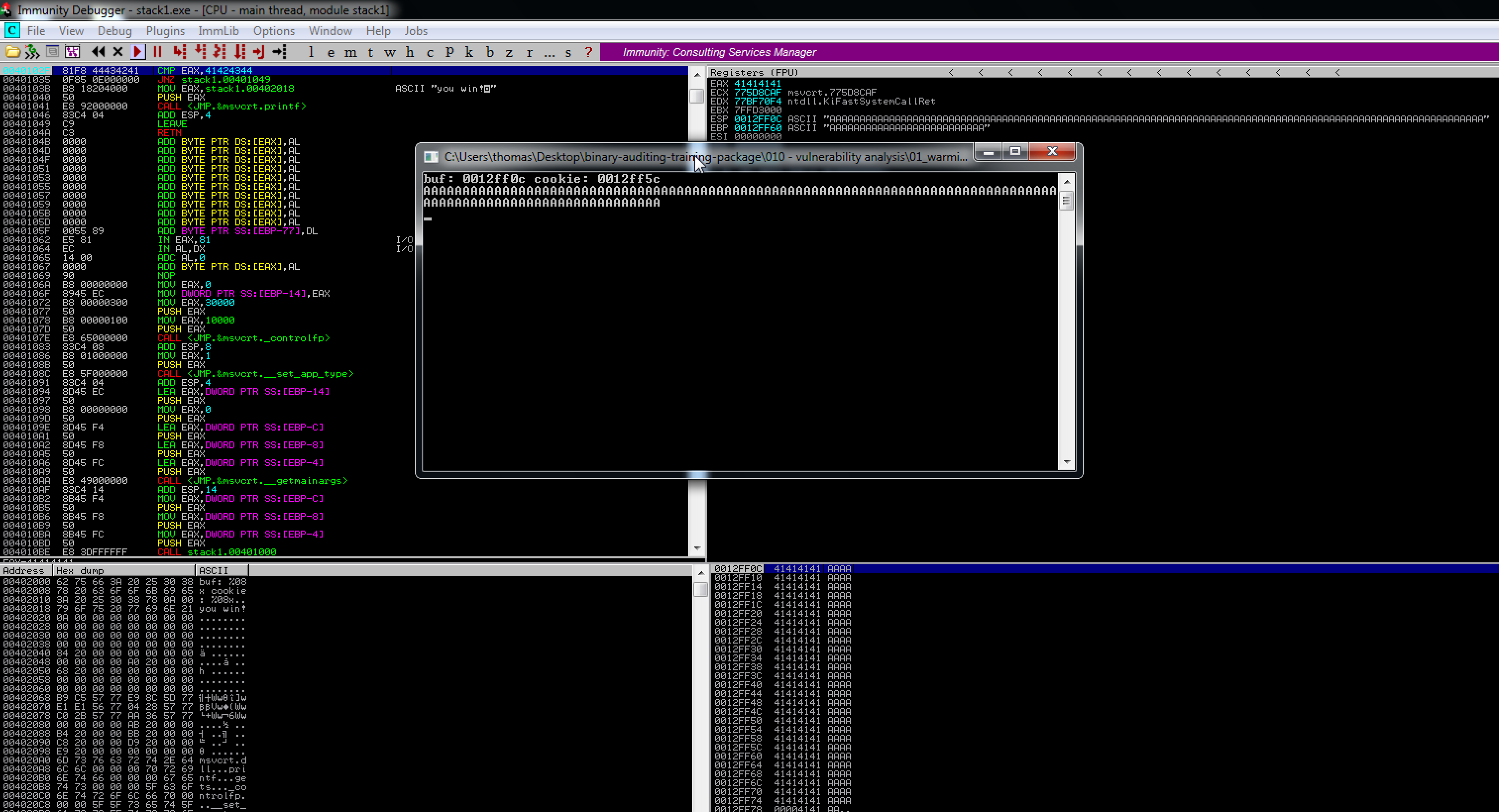
Now that I know I can overwrite eax by just entering 84 chars, I need to account for little endian when the bytes get written to the stack. So 80 As followed by 'DCBA'.