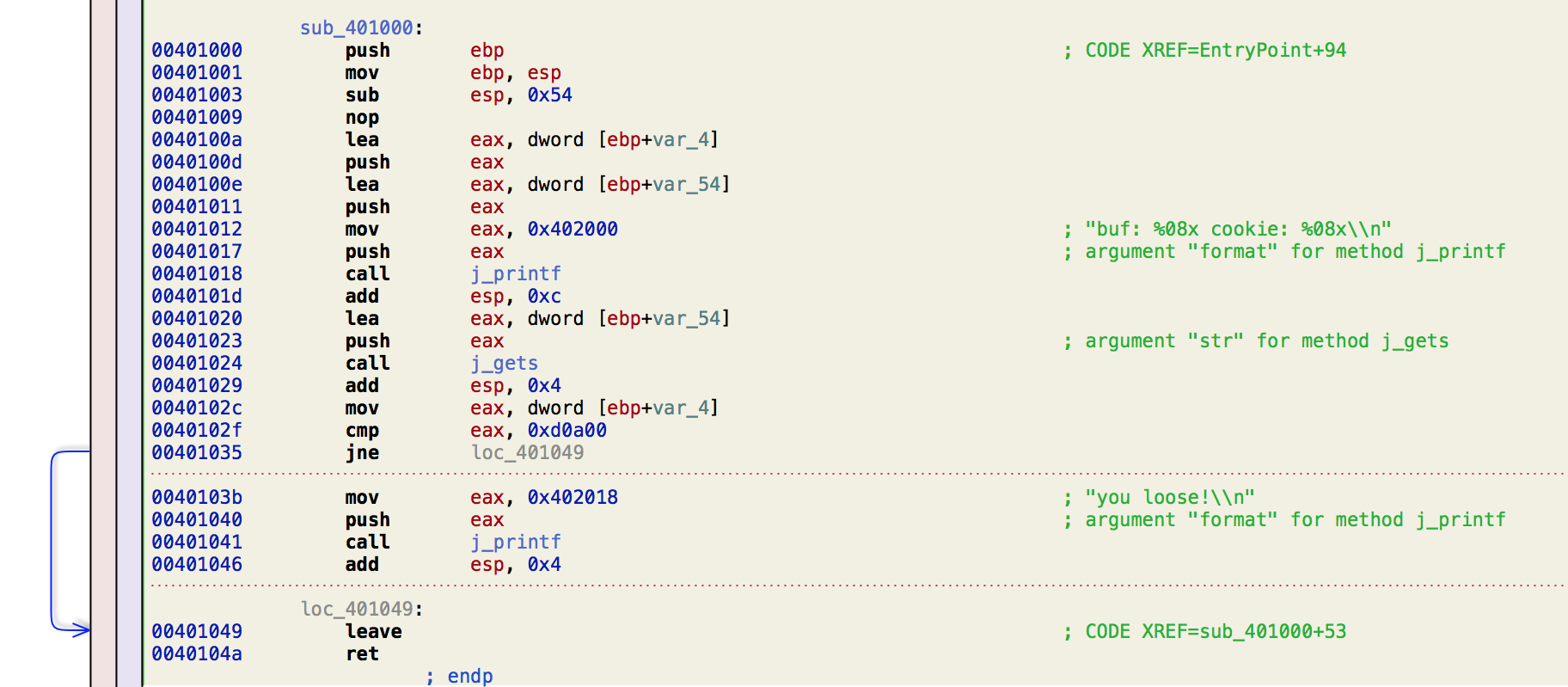
Opening up the stack5 executable, we can quickly see that the value compared is the exact same as stack4 however, we are presented with a nice 'you loose!' (typo?) message instead.
Seeing that there wasnt any jumps to a 'you win!' message, I decided that this may be a binary patching challenge.
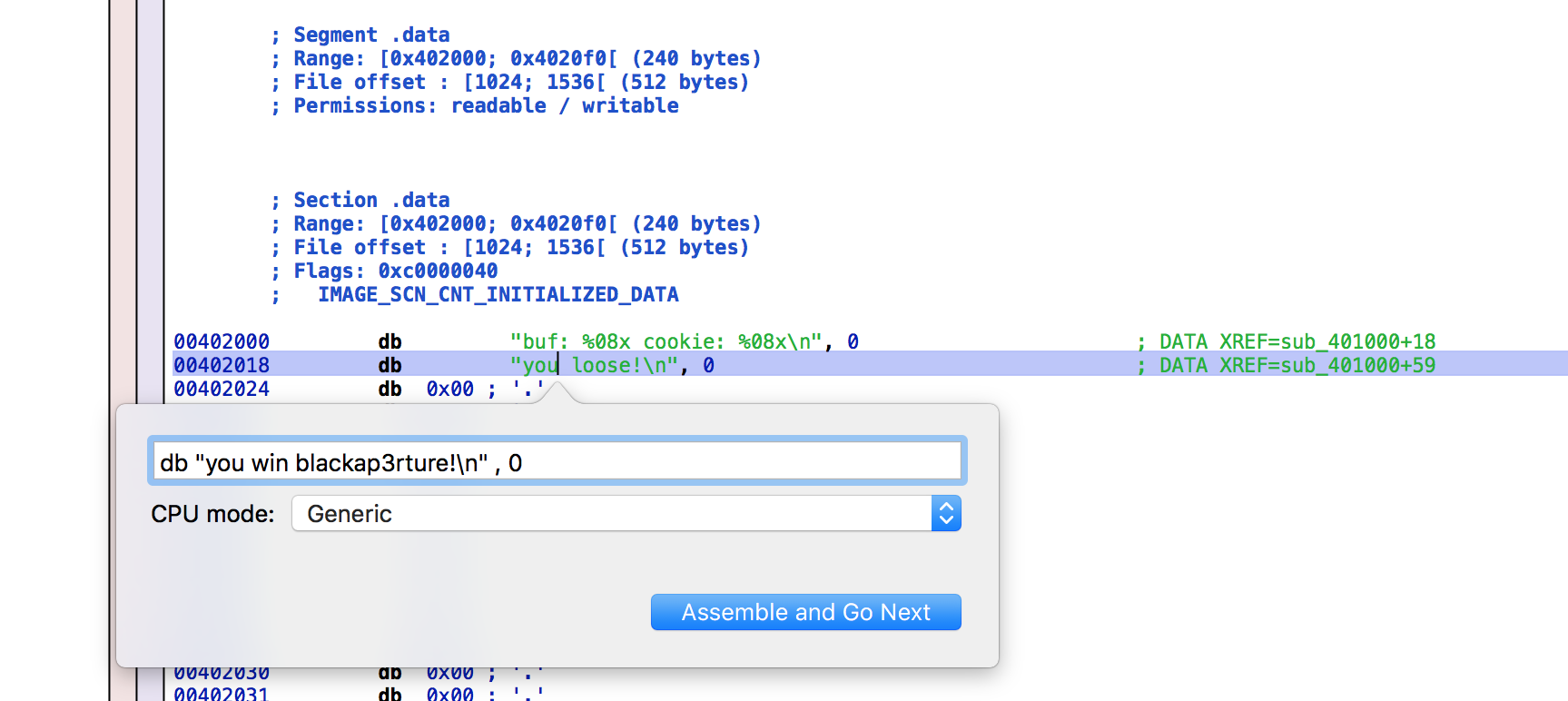
Now your disassembler may be different on how to go about changing the assembly, but using Hopper we can navigate to the Data Section, select the text we want to change, and then Modify --> Assemble Instuction.
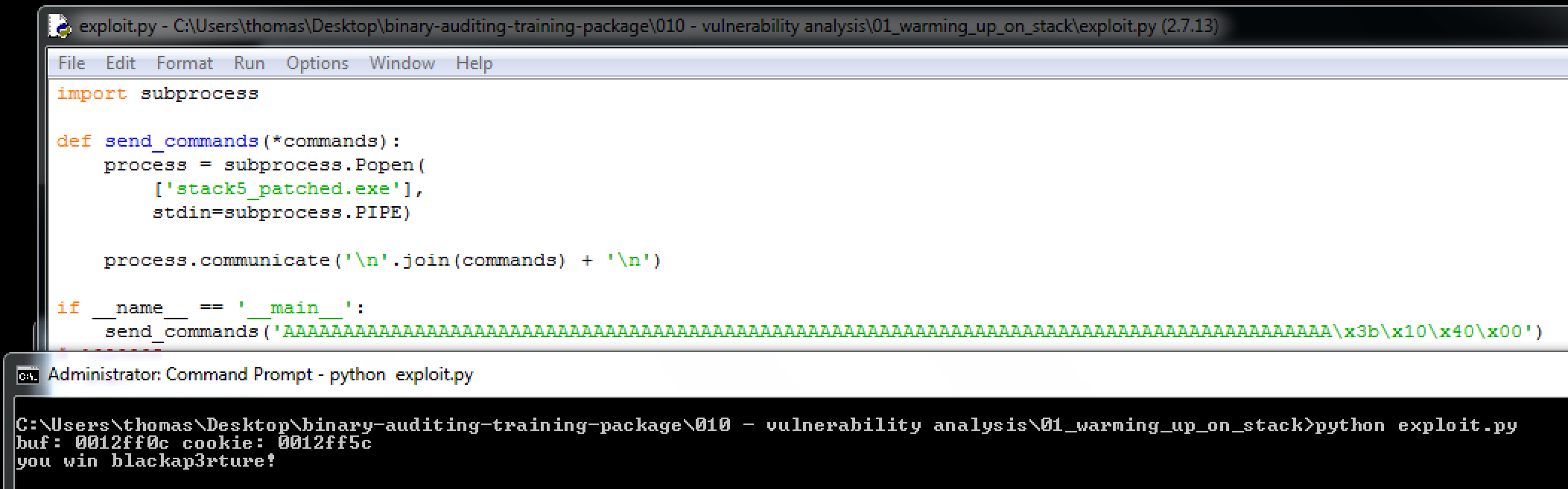
Following the same format, I entered the text I wanted displayed...
Again using the same payload as the stack4 challenge, we are now presented with our own text.